Strategize and Range WITh Proven IT Managed Providers Methods
In the busy landscape of modern service, the tactical usage of IT took care of services has come to be a keystone for companies intending to boost operational effectiveness and drive sustainable growth. By implementing tried and tested methods customized to meet certain service requirements, business can navigate the intricacies of technology while staying affordable and agile in their particular industries.
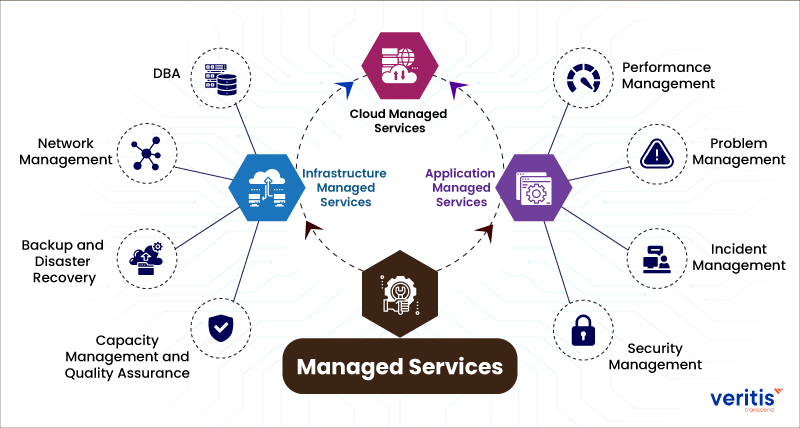
Advantages of IT Handled Services
Undoubtedly, the advantages of IT Managed Providers are critical in enhancing organizational performance and minimizing downtime. By outsourcing IT management to a specialized service provider, services can take advantage of a wide range of know-how and resources that would otherwise be expensive to maintain in-house. One of the crucial advantages of IT Took care of Solutions is positive monitoring and maintenance of systems, which helps stop potential problems prior to they intensify right into major issues. This positive technique converts into better system uptime, minimized downtime, and boosted overall productivity for the organization.
Moreover, IT Managed Provider can supply access to the most recent innovations and best methods without the need for consistent investment in training and framework upgrades. This guarantees that businesses stay competitive in a quickly evolving technological landscape. Additionally, by offloading regular IT tasks to a taken care of companies, interior IT groups can focus on calculated initiatives that drive advancement and development for the organization. Finally, the benefits of IT Managed Solutions are crucial in improving procedures, boosting effectiveness, and inevitably, driving business success.
Key Methods for Execution
With an understanding of the significant benefits that IT Took care of Services offer, services can currently concentrate on implementing essential methods to successfully incorporate these solutions right into their procedures. One essential technique is to clearly specify the extent of solutions required. This includes performing a complete analysis of existing IT infrastructure, identifying pain points, and setting particular goals for improvement. Furthermore, services should develop clear interaction networks with their managed provider to ensure seamless partnership and prompt issue resolution.
Another essential approach is to focus on cybersecurity measures. Data violations and cyber dangers pose substantial dangers to organizations, making protection a top concern. Executing durable safety and security methods, regular surveillance, and timely updates are crucial action in guarding sensitive details and maintaining service continuity.
Moreover, businesses ought to develop service level arrangements (SLAs) with their managed solution carrier to define assumptions, duties, and performance metrics. SLAs assist in establishing clear guidelines, making sure liability, and maintaining service top quality standards. By integrating these vital strategies, services can leverage IT Handled Services to enhance procedures, enhance effectiveness, and drive lasting development.
Taking Full Advantage Of Performance Via Automation
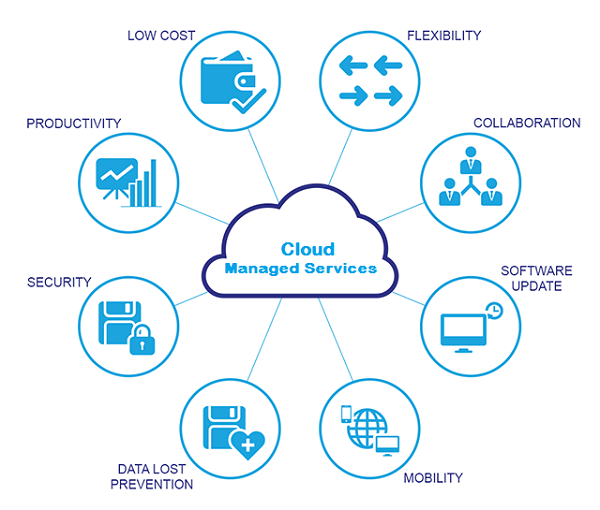
Moreover, automation enables real-time review surveillance and information evaluation, supplying useful insights for informed decision-making. By automating regular tracking tasks, companies can proactively address issues prior to they intensify, reducing downtime and optimizing efficiency (it managed service providers). Additionally, automation can promote the seamless integration of various systems and applications, improving collaboration and information flow throughout the organization
Ensuring Data Protection and Compliance
Data protection and compliance are vital concerns for services running in the digital landscape these days. With the raising volume of delicate information being stored and refined, making certain robust safety measures is important to guard against cyber risks and comply with regulatory demands. Executing detailed data safety and security practices involves encrypting data, establishing gain access to controls, routinely upgrading software program, and performing security audits. Additionally, adhering to laws such Read Full Article as GDPR, HIPAA, or PCI DSS is necessary to keep and stay clear of pricey fines trust fund with consumers. Handled IT providers play an important role in helping businesses browse the facility landscape of information safety and compliance. They provide proficiency in implementing security methods, checking systems for possible breaches, and guaranteeing adherence to industry laws. By partnering with a reputable took care of companies, companies can enhance their information safety position, mitigate threats, and demonstrate a commitment to protecting the discretion and stability of their data possessions.
Scaling IT Infrastructure for Development
Including scalable IT infrastructure options is essential for assisting in organization growth and operational effectiveness. As firms expand, their IT needs progress, calling for infrastructure that can adapt to raised needs perfectly. By scaling IT facilities properly, companies can ensure that their systems stay trustworthy, secure, and performant even as workloads grow.
One trick facet of scaling IT infrastructure for growth is the ability to flexibly assign sources based upon existing needs. Cloud computing services, as an example, deal scalability by permitting organizations to readjust storage space, refining power, and various other sources as required. This flexibility makes it possible for companies to efficiently manage spikes sought after without over-provisioning resources during periods of lower task.
In addition, implementing virtualization modern technologies can improve scalability by making it possible for the creation of digital instances that can be easily copied or changed to accommodate changing workloads - it managed service providers. By virtualizing servers, storage, and networks, organizations can optimize source use and streamline IT management procedures, eventually supporting company development campaigns properly
Final Thought
Finally, implementing IT took care of solutions can bring various benefits to a company, such as enhanced efficiency, boosted information safety, and scalability for growth. By adhering to crucial techniques for execution, using automation to make best use of effectiveness, and guaranteeing information safety and why not try here compliance, services can better plan and scale their IT infrastructure. It is critical for companies to evolve and adjust with technological innovations to stay affordable in today's ever-changing landscape.